Fun to see
deep packet inspection (DPI) becoming a topic of everyday conversation as it gets applied to survey, and possibly in the future shut down, file sharers - a service of
Detica coming to a
Virgin ISP near you....
A major challenge for the commercial sector for years has been the growth in SSL traffic crossing firewalls being annoyingly opaque to deep packet inspection. (The only real solution is one that cracks open the packets by decrypting using"SSL Inspection Appliances" from the likes of
Netronome,
Blue Coat, et al.)
So on the one hand DPI is a tool for surveillance of unencrypted just as the amount of encrypted traffic is growing; and how long before those file sharers adopt it - oh
they have already since 2005. On the other hand maybe if we all adopted encryption for all traffic, perhaps serviceproviders in future might
avoid £8000 fines- could it possibly reinstate them as "
common carriers" if they
require users to encrypt all traffic.
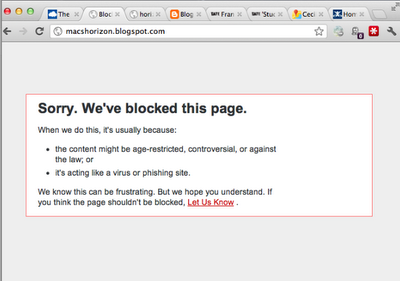
"Dear Blogspot, can I please be accessible as
https://machorizon.blogspot.com ..."
Written on December 7, 2009





 Copy of an
Copy of an 




 Maurizio Pilu
Maurizio Pilu 









 RIP Google Health and Powermeter (
RIP Google Health and Powermeter (