Privacy sometimes means secrets
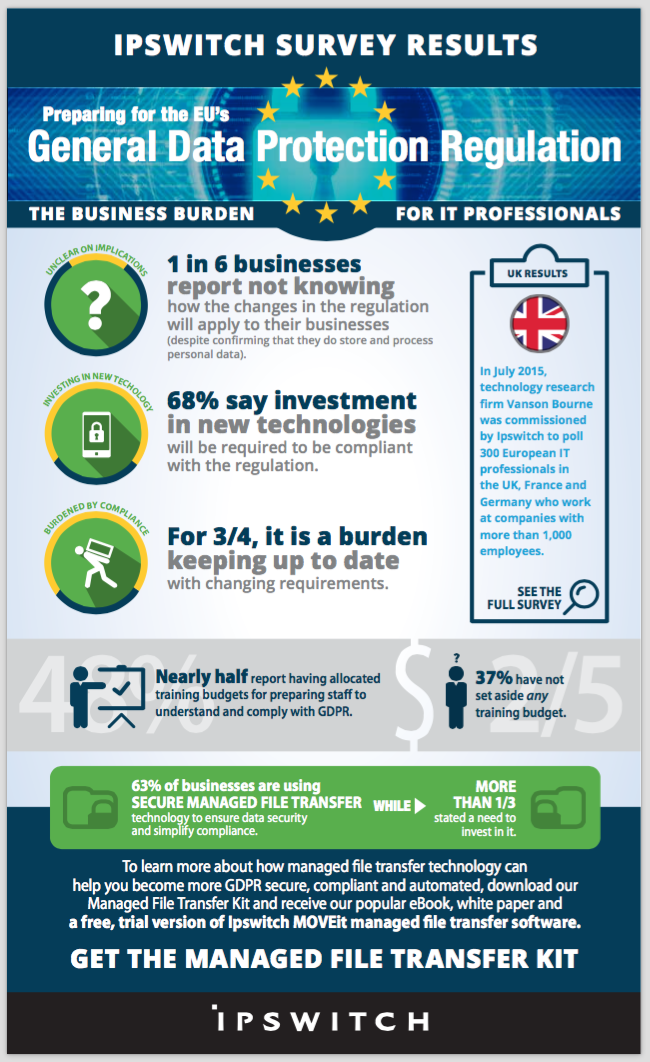 A recent survey (Sep 2015) for IPSWITCH was broadly picked up by the tech press and highlighted the concerns of IT professionals with the looming EU General Data Protection Regulation (GDPR); 69% say their business will need to invest in new technologies or services to help prepare the business for the impact of GDPR including:
A recent survey (Sep 2015) for IPSWITCH was broadly picked up by the tech press and highlighted the concerns of IT professionals with the looming EU General Data Protection Regulation (GDPR); 69% say their business will need to invest in new technologies or services to help prepare the business for the impact of GDPR including:- 62%: encryption
- 61%: analytic and reporting
- 53%: perimeter security
- 42%: file sharing
That said these two stories relate to only two of the eight principles (also see below) of the Data Protection Act in the UK, the remaining six presenting us with a whole series of further challenges to compliance. And that's the 1998 act, not even the pending GDPR.
Perhaps the increasing costs and complications of processing Personal Data might lead us to ask some questions about how we design at least some of our future IT systems to avoid the issue in the first place. In particular within the domain of the Internet of Things, there is a widespread presumption that the value in the data that the things communicate is only realised when simultaneously the data is shared (with a 2nd, possibly 3rd party) and the person identified. We need to challenge this assumption from the perspectives of both the technology and the business model.
Projects such as the hoax drug testing toilet and the IoT toilet roll holder raise plenty of questions around sharing data that we would do well to keep in mind before building technology that at its heart presumes sharing is a good idea (*).
So IoT developing folks ask yourselves some questions:
(*) If you need a daily reminder of some of the lunacy out there, follow @internetofshit (too much toilet humour. ed.).
Projects such as the hoax drug testing toilet and the IoT toilet roll holder raise plenty of questions around sharing data that we would do well to keep in mind before building technology that at its heart presumes sharing is a good idea (*).
So IoT developing folks ask yourselves some questions:
- Does this heating control accessible from a roaming mobile phone need to pass unencrypted data through a middle man, or should we take a leaf out of iMessage's book and just encrypt it end-to-end?
- Ditto baby monitors.
- Does this thermostat really need to know who I am, with name, address, etc or could it simply operate anonymously?
- Smart washing machine doing condition monitoring - yes supply anonymous statistics of operation to the manufacturer, but maybe a monthly digest rather than a second by second stream of washing machine consciousness... in fact why not use email to send it and bcc me?
- What value do you derive from data fusion across users - or is it simply that you wanted to obtain an even more detailed profile of me to sell to marketeers?
(*) If you need a daily reminder of some of the lunacy out there, follow @internetofshit (too much toilet humour. ed.).
From the ICO website...
- Personal data shall be processed fairly and lawfully and, in particular, shall not be processed unless:(a) at least one of the conditions in Schedule 2 is met, and (b) in the case of sensitive personal data, at least one of the conditions in Schedule 3 is also met.
- Personal data shall be obtained only for one or more specified and lawful purposes, and shall not be further processed in any manner incompatible with that purpose or those purposes.
- Personal data shall be adequate, relevant and not excessive in relation to the purpose or purposes for which they are processed.
- Personal data shall be accurate and, where necessary, kept up to date.
- Personal data processed for any purpose or purposes shall not be kept for longer than is necessary for that purpose or those purposes.
- Personal data shall be processed in accordance with the rights of data subjects under this Act.
- Appropriate technical and organisational measures shall be taken against unauthorised or unlawful processing of personal data and against accidental loss or destruction of, or damage to, personal data.
- Personal data shall not be transferred to a country or territory outside the European Economic Area unless that country or territory ensures an adequate level of protection for the rights and freedoms of data subjects in relation to the processing of personal data.
Written on October 8, 2015
